How Do Vpn & Tor Work

If you worry that your internet service provider will monitor your online activity, you may be using privacy tools like Tor or VPN services. But don’t you often wonder how they work to build tunnels that prevent internet history tracking? So this article explains how tor and vpn work.
VPN
A VPN, or virtual private network, establishes a secure connection over an unprotected network by changing location, encrypting data, and protecting user privacy.
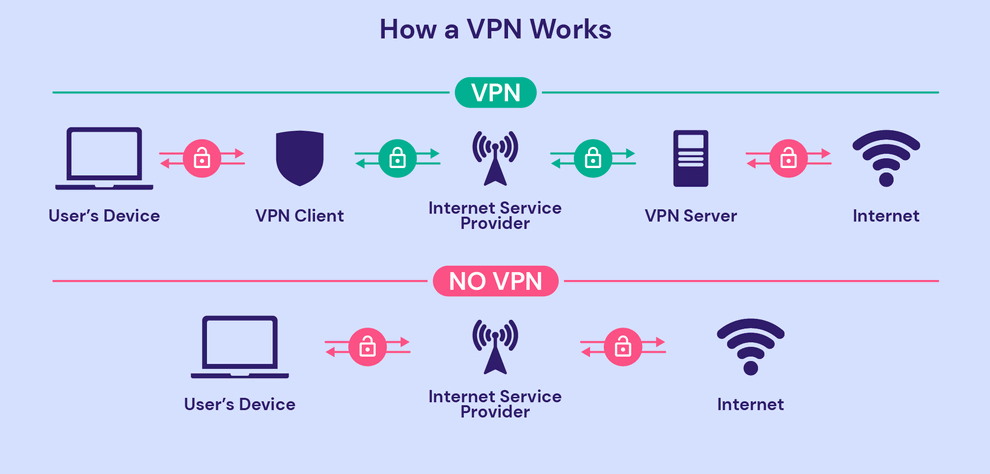
- WiFi security in public places:
Public wifi is free, but as we all know, everything has a price. Public wifi comes with a number of security risks, including virus attacks and data breaches, all of which are extremely risky. It is especially vulnerable to man in the middle attacks. In these situations, using a VPN can be helpful because it offers a safe and secure tunnel for your online activities and also hides your identity.
- Access to any content across the globe:
Let’s say you want to use an application like tiktok or watch a movie on Netflix that isn’t available in your country. Then, utilising a VPN, one may access the content with ease because the VPN alters your current location and lets you request the content as if it were from another area. The majority of movie-goers employ this approach to get the movie they desired.
- Data privacy from your government and Internet service provider:
There is still a potential that you could be attacked even though you are still connected to your home network. Additionally, your ISP (internet service provider) may sell the information about your web activity to advertisers, the government, or it could be hazardous if it falls into the wrong hands in the event of a data breach. VPN might be a wise investment in protecting your data if you are concerned about governmental overreach, the disclosure of your IP, or being watched by your ISP.
- Security when working remotely:
If you’re an individual considering purchasing a VPN for your business, one advantage is that employees can access your office network and view confidential documents on their personal devices while they’re not at work. Since remote work may still be an option even after the pandemic is over, investing in a VPN will help keep sensitive information safe off-site.
- Subsidized travel and shopping:
Research has shown that hotel and flight prices differ depending on your location, therefore using a VPN to change your location can also be advantageous when making travel plans.
Tor
To keep their online activities hidden from their ISPs, governments, and attackers, onion router, also known as tor, is utilised by cybercriminals and even regular people around the world.
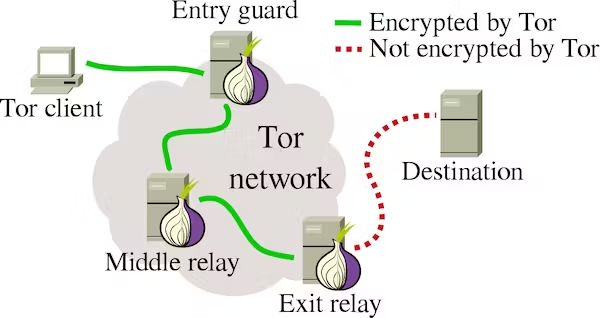
How do they work?

As seen in the image above, the internet is initially represented by a small cup of water that contains all the websites, YouTube, Google, and a tube or tunnel that serves as our internet service provider. Since the ISP can monitor our online activity, we now use a vpn or tor as a straw to create a tunnel through the tube so that when we go to drink or browse the internet, we are no longer being monitored.
In short, The ability to access the internet is provided by your internet provider, and vpn or tor then establishes a tunnel so that nothing outside of it, including your internet services provider, is able to track your data and sell it to third parties.