What is Dark Web?

You’ve undoubtedly heard of the dark web, and I’m sure you’ve also heard that it’s where people go to buy and sell illegal products like drugs, weapons, and other items, as well as to hire hit men and other unlawful activities. But wait, there’s more to it than that—the dark web can be beneficial as well. I thus came up with this post about the dark web, which discusses its applications, and additional details about it.
Dark Web?
The dark web is a section of the internet that is hidden from search engines and can only be accessed with the anonymizing Tor browser.
Over a five-week period in 2015, researchers Daniel Moore and Thomas Rid of King’s College in London categorized the content of 2,723 active dark web sites and discovered that 57% host illegal materials.
Credit card numbers, various drugs, weapons, fake cash, stolen login credentials for Netflix, and software to break into other people’s computers are among things that can be purchased. You can pay hackers to attack systems for you.
The dark web has a valid aspect as well; not everything on it is illegal. For example, you can sign up for a chess club or BlackBook, a social network known as “the Facebook of Tor.”
How Dark Web Differs from Clear and Deep Web?
Before learning more about dark web, let’s first understand how the internet is divided into three separate parts known as the Clear Web, the Deep Web, and the Dark Web.
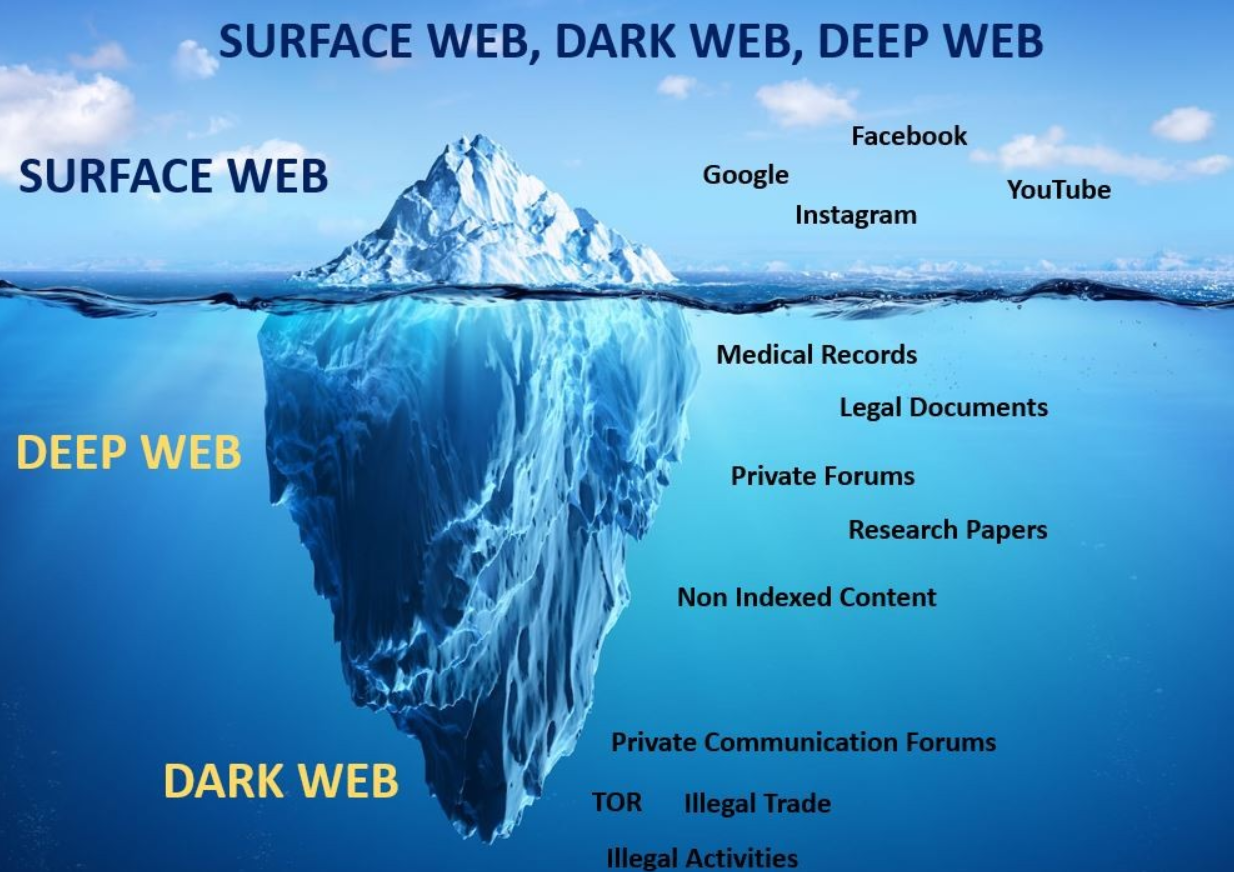
Clear Web
As illustrated in the image, A clear web represents the resources on the internet that is available to everyone. For instance, this website where you are reading an article about the dark web, YouTube, Instagram, Facebook, Google, and and so on.
Deep Web
Again, if you look at the image above, you will notice that the deep web is below the water, or below the level of the horizon, indicating that it is concealed and accessible to those with the proper authorization.
This is easily understood by using an example: suppose you install the social media app Instagram, which is an example of clear web, and the moment you create and login into your account, you enter deep web, where the person accessing requires authentication and authorization. Other examples of the Deep Web include medical records, legal documents, private forums, research papers, and more.
Dark Web
The Dark Web, the part you’ve all been waiting for, is finally here. Judging from the image above, we can see that the Dark Web extends much deeper into the Deep Web.
Though we already read a brief overview of the dark web in the introduction, let’s learn a little bit more. There are search engines for the Dark Web, but the majority of the time, you’ll need to know the specific URL to locate a site. Instead of Clear Web The top-level domain like “.com” or “.in,” websites on the Dark Web use the “.onion” TLD.
Although accessing the Dark Web is not illegal, there is a lot of unlawful stuff there, and engaging with it or watching it could be considered to be doing an illegal act.
The Good Side
There is a misconception that using and accessing the dark web is illegal and sinister. Although some of the content on the dark web may be problematic and not all of it is illegal, there are many acceptable purposes for it, such as helping people in avoiding government censorship, to providing an additional layer of anonymity to email services.
Here are a few acceptable justifications for using the dark web:
- Bypass restriction by the government:
Governments all across the world make an effort to limit what their people can see online. A citizen’s internet actions can be hidden from a government that is watching them via the dark web. Users could conceal information such as the websites they viewed and their location by using the dark web.
- Email services with anonymity:
While there are many encrypted email services on the surface web, those seeking even more anonymity should visit the dark web. ProtonMail, which is supported by the Tor network and safeguards user privacy, and fights censorship, is the most well-known email service available on the dark web.
There are additional dark web-only email providers; the most popular ones are Mail2Tor and Torbox, both of which require the Tor browser to use.
- Social Media Access:
Most people who have internet access have a social media account on at least one of the most well-known sites, including Facebook, Instagram, or Twitter.
Unexpectedly, some of our favorite surface-web social media companies, like Twitter and Facebook, have opened mirror sites on the dark web for users who want to avoid tracking by the government.
- Forums and Chat Rooms:
The dark web is home to chat rooms and forums that unite communities that want to communicate anonymously about topics they might otherwise feel uncomfortable discussing.
Paradise is one of the most well-known forums on the dark web, where members may talk about social concerns and difficulties in the world while remaining anonymous.
The Bad Side
Now that we’ve seen the positive aspects of the dark web, let’s explore its most intriguing and risky aspects. Unlawful markets do exist on the dark web. Yes, they provide every product you’ve ever heard of. weapons, drugs, services, violent content, and humans.
It may be against the law to visit these sites. Law enforcement is actively seeking to find and bring to the courts those who purchase, sell, or distribute unlawful material on the dark web.
The following are the two most harmful outcomes of using the dark web without taking any safety measures and purposefully consuming inappropriate content:
-
If you accidentally click on a link that loads explicit content like child pornography, you are responsible for it and may face legal action.
-
A single incorrect link-click can cause your computer to become infected with malware that can steal or encrypt your files and launch second-stage attacks like blackmail.
Accessing the Dark Web
The TOR browser will be used to access the dark web. The following are instructions on how to set up the Tor browser and how to use the Dark Web safely:
Downloading the TOR Browser
Download the TOR Browser for your OS by going to the TOR Project website (here). Android, Windows, Mac OS, and Linux are all supported by the browser.
Once you’ve finished downloading and running TOR Browser, you should see something similar to what is seen below.
Browsing Clear Web Sites
The only thing that changes when we use the TOR Browser to access “normal” websites is that we have more privacy because websites cannot follow us using cookies, and the browser automatically deletes our browsing history.
For instance, we can use the default privacy-friendly search engine Duck Duck Go to search for “YouTube” or “GeeksforGeeks” and visit their website.
Browsing Dark Web Sites
The wait was worthwhile. Here we are, using the TOR Browser, to visit the dark websites. We will visit a few websites that are known to be secure below.
And I advise you not to visit any inappropriate unlawful websites because law enforcement agencies all around the world keep an eye on connections to these sites, and even though accessing them is questionable, doing so could expose you to view illegal or disturbing content.
Additionally, use a virtual Windows machine instead of visiting these dark websites on your host computer because some of the malicious websites might compromise your host system. However, if they do compromise the virtual Windows machine, you can safely uninstall and reinstall them without affecting your host machine.
Important Detail Regarding Dark Web Site Accessibility: Due to the nature of the Dark Web, many websites do not operate continuously, hence the websites mentioned in this article could go offline either temporarily or permanently.
- Facebook on the Dark Web!
Yes, even Facebook has a site on the dark web. Copy the following URL and paste it into the top address bar of TOR: https://www.facebookwkhpilnemxj7asaniu7vnjjbiltxjqhye3mhbshg7kx5tfyd.onion
You may be curious as to why Facebook has a mirror site. It is due to the fact that few government cencorship lead to site blocking at the national level, a practice commonly referred to as “blocking sites on the great firewall”. Anyone, anywhere, can access Facebook via TOR because the request is not being blocked.
- CryptoStorm - a VPN Service Provider!
Open-source VPN provider CryptoStorm uses an advanced token-based methodology. In addition, the company has made a significant investment in offering its subscribers a variety of anonymous payment options. The good news is that it has a mirror site as well.
Copy the following URL and paste it into the top address bar of TOR: http://stormwayszuh4juycoy4kwoww5gvcu2c4tdtpkup667pdwe4qenzwayd.onion/
Although we are aware that Tor is generally secure in terms of privacy, adding an additional layer of privacy may help us become more anonymous. So, we can utilise both Tor and a VPN simultaneously. The first approach involves connecting to a VPN server before connecting to the Tor network. In this scenario, neither the Tor entry node operator nor your ISP will be aware that you are utilizing Tor.
- DEF CON - a Hacker Conference
DEF CON is a hacker conference held annually in Las Vegas, Nevada. Its attendees include computer security experts, journalists, lawyers, federal government employees, security researchers, students, and it also has a mirror site on Tor.
Copy the following URL and paste it into the top address bar of TOR: http://g7ejphhubv5idbbu3hb3wawrs5adw7tkx7yjabnf65xtzztgg4hcsqqd.onion/
- Central Intelligence Agency (CIA)
The CIA is the United States government’s primary international intelligence and counterintelligence agency.
The information, contacts, and services available on the CIA’s main website are also available on its “onion” website. It is aimed at persons who want to exchange information with the CIA anonymously but are concerned about being traced.
Copy the following URL and paste it into the top address bar of TOR: http://ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion/
Conclusion
Guys, we’ve learnt a lot about the dark web, from “what” to “accessing onion sites”.
I hope you enjoyed learning!